Onion Routing: What is Tor and How Does it Work
Onion routing has been around for decades as a free, decentralized, peer-based communication technique over the world wide web. Tor, the most well-known implementation of the onion network, has also been in use since the early years of this millennium. It is one of the best ways to maintain anonymity online. So here’s what you need to know about Tor, onion routing and online privacy.
What is Tor?
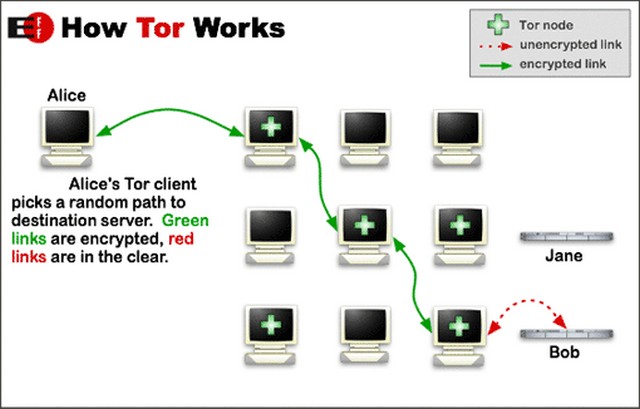
Tor is an open-source, decentralized privacy network that enables users to browse the web anonymously. Short for ‘The Onion Router’, it is a secure, encrypted networking protocol to ensure online privacy. It does so by using ‘onion routing’ – an anonymity technique that transmits data through a series of layered nodes, or servers, to hide the user’s IP address from not only the website or service being accessed, but also government agencies and organizations trying to monitor network traffic. It also prevents the ISP or others from snooping on the user’s online activities.
What is Onion Routing?
Onion routing is a technique for anonymous communication over a computer network by using a series of random “nodes”, or servers, to relay messages. Unlike regular proxies or VPNs, which typically use a single server to route your communication, onion routing uses multiple (largely crowdsourced) servers. This makes it incredibly difficult for would-be eavesdroppers to trace the original sender. All communication is hidden behind multiple layers of encryption at the original entry node (your computer). It is then decrypted one layer at a time at every exit node it passes through, before being fully decrypted for the final exit node – the website or service you’re trying to access. The original message remains hidden while being transferred from one node to the next. It means no intermediary knows both the origin and final destination of the data. This is what enables privacy and allows the sender to remain anonymous.
Origins and Implementations
Onion Routing, the underlying anonymity technique for Tor, was initially developed in the mid-1990s by the US Navy for confidential government communications. Paul Syverson, a computer scientist working with the US Naval Research Academy, is widely credited as being the inventor of Onion Routing. The research was subsequently published in the IEEE journal of communications in 1998. Tor, which has since become the most widely-used onion routing technique, was also developed by the US Navy and released under a free license in 2002. The software is now developed and maintained by the Tor Project, a non-profit organization founded in 2006 by two of the original Tor developers, Roger Dingledine and Nick Mathewson, alongside five others. The main implementation of Tor is written in C, along with Python, JavaScript, and several other programming languages. The project is funded by EFF and several other leading organizations advocating digital freedom and online privacy. It is widely used by activists, journalists, whistleblowers and ordinary internet users for safeguarding privacy, protecting intellectual freedom and circumventing censorship.
Applications
Tor enables users to access any website or online service they can access on the ‘clearnet’ (regular web). In addition, it also allows users to access the ‘hidden web’ that contains websites with a .onion top-level domain (TLD) name, designating an anonymous onion service. Part of the so-called Deep Web, .onion addresses are not actual DNS names, and the TLD is not in the Internet DNS root. These sites can only be accessed by routing traffic through the Tor network. It can be done either by using the Tor Browser or through the standalone Tor client.
Tor Browser
The Tor Browser is the official web browser developed and distributed by the Tor Project. Based on the source code of Mozilla Firefox, it is a free and open-source software that retains many of the privacy features of its parent, but comes with a built-in Tor client that starts by default every time you fire it up. It is known to be used not only by ordinary privacy-conscious users, but also by journalists reporting on sensitive matters, political activists fighting against repressive regimes and whistleblowers fearing adverse repercussions for their revelations.
With all communications being routed through the Tor network by default, the Tor Browser prevents anyone, including internet service providers (ISPs), advertisers, the government, and anyone else, from monitoring your connection and seeing which websites you visit. The Tor Browser comes with HTTPS Everywhere, NoScript and other Firefox add-ons to protect your privacy and security. It also blocks unsafe plugins like Flash, RealPlayer, QuickTime, and others that can be manipulated into revealing the user’s IP address.
Platforms and Availability
The Tor Browser is available on Windows, Linux, macOS (download for desktops), and Android (download from Google Play). There is no official version of Tor for iOS yet, though The Tor Project recommends the Onion Browser on iPhones and iPads (download from the App Store). It is also not officially available on Chrome OS, but you can use the Android app on Chrome OS. Other privacy-focused applications, like Brave Browser, also recently implemented Tor integration to boost privacy. Tor Browser on Android Meanwhile, if you want to route all your traffic through Tor for ultimate privacy, you may also use a portable Linux distro called Tails. It is built upon Debian and routes all traffic through Tor by default. The operating system can be booted directly from a USB stick, so even if something goes wrong, all you’ll need to do is reboot or even re-format the USB drive to mitigate the problem. On Windows and other platforms, you can either use the Tor Browser Bundle or download the standalone Tor client.
Drawbacks, Controversies and Criticisms
Tor has been praised by technologists, privacy advocates, and human rights groups for providing anonymity to political activists living under repressive regimes, and general web users seeking to circumvent censorship. However, even as free-speech advocates heap praises on it for bringing digital privacy to activists and reporters, the technology has its own share of detractors, who criticize it for various reasons. Some believe that it is not as safe as The Tor Project claims it is, citing the US law-enforcement’s actions against onion sites, such as web-hosting company, Freedom Hosting, and notorious dark web marketplace, Silk Road. Others, mainly government agencies like the US National Security Agency (NSA), have criticized the technology, calling it a “major threat” to its monitoring of terrorists and other potential security threats. Tor may be one of the best options for maintaining anonymity online, but it comes with its own share of problems. Here are some of its most notable drawbacks:
1. Exit Node Eavesdropping
Contrary to popular belief, Tor itself isn’t anonymous enough. Like other low-latency anonymity networks, Tor does not protect against the monitoring of traffic entering and exiting the network. As a result, the network is theoretically susceptible to exit node eavesdropping, traffic analysis attacks, mouse fingerprinting and circuit fingerprinting, among other vulnerabilities.
2. Sluggish Connection Speeds
Another major disadvantage of Tor is sluggish connection speeds, which is a product of how the technology is designed. Since traffic in Tor is relayed through so many nodes, it can take a while to load website content. This can be frustrating even for seasoned users who know what to expect. Like torrent, the speed depends on the number of nodes and increases with the number of users hosting a relay.
3. Restrictions
Some websites and online service providers block access to Tor or require users to fill in Captchas before they can access the site. Premier CDN service provider, CloudFlare, routinely uses Captchas and other restrictions on traffic coming through the Tor network, citing malicious traffic. While it is an essential protection against possible DDoS attacks by botnets, it can further reduce the surfing experience for users.
4. Poisoned Nodes
While cases of users being de-anonymized because of a Tor vulnerability are almost unheard of, law enforcement agencies and hackers can still monitor users for surveillance or espionage purposes by running ‘poisoned nodes’, or gateways that are created specifically to monitor Tor traffic. For example, an attacker running two poisoned Tor nodes – one entry and one exit – will be able to analyze traffic and identify the tiny fraction of users whose circuit happened to cross both of those nodes.
How Tor Can Aid Your Online Privacy
With tens of thousands of nodes operating, the chances of getting de-anonymized because of poison nodes are less than one in a million. When Tor users are arrested for abusing their anonymity to commit crimes, it is often due to human error rather than any inherent weakness in the core technology. In theory, Tor cannot stop malicious actors from targeting you, nor the law enforcement from tracking you if they thought you were a ‘person of interest’. That said, when used in conjunction with other privacy tools, such as OTR, Cspace, ZRTP, RedPhone, Tails, and TrueCrypt, Tor will almost certainly help you boost your privacy. To preserve your online anonymity or circumvent censorship, you can also use VPN services, many of which are available for free. Make sure you pick one that doesn’t keep any log related to traffic, session, DNS or metadata. My personal favorite is Cyberghost, but there are many other excellent services that you can subscribe to.
Q. Why does Tor take so long to load sites?
By design, Tor relays your traffic through volunteers’ servers in various parts of the world. That creates its own bottlenecks and increases network latency. You can help improve the speed of the network by running your own relay.
Q. Is Tor safe?
Tor is free and open source, and is routinely audited by experienced programmers and volunteers from around the world. As such, it is one of the safest and most secured ways to enhance your privacy online. However, do note that it does not protect all your internet traffic. It only protects applications that are properly configured to send their Internet traffic through Tor.
Q. Is Tor illegal?
Tor is not illegal anywhere in the world, so using Tor by itself is fine. If anyone running a relay node gets into trouble over abuse issues related to third-party users, they can resort to a web service called Exonerator that can check if an IP address was a relay at a given time. The Tor Project also provides a signed letter to back that up.
Q. What is Tor used for?
Tor is used by technologists, privacy advocates, and ordinary users to preserve their online anonymity and digital privacy. It is one of the main tools of secured communication for political activists living under repressive regimes and general web users seeking to circumvent censorship.
Q. Does Tor hide IP address?
Tor uses an anonymity technique called ‘onion routing’ that transmits data through a series of layered nodes to hide the user’s IP address from not only the website or service being accessed, but also government agencies or organizations trying to monitor network traffic.
Q. Does Tor hide my location?
Tor hides your location, your IP address, and other personally-identifiable information. The exit node only gets to see your user agent (browser), which, by itself, is not personally-identifiable data. However, other apps on your PC, including browser add-ons, website cookies and other software, might reveal more about your identity. Which is why, you should use the Tor Browser, which comes with built-in safeguards against such issues.
Q. Is it safe to use Tor on Android?
The Tor Browser on Android uses the same onion routing technique as the desktop clients. So yes, it is as safe on Android as it is on any other platform.
Q. Does Tor leave anything on your computer?
As long as everything is correctly configured, Tor leaves no trace of your online activities on your computer or anywhere else.
Q. Does my ISP know I’m using Tor?
Both your ISP and the website(s) you’re visiting will know that you’re using Tor. However, your ISP will not be able to detect which services you’re connecting to, nor will the website be able to tell who your are and where you’re connecting from. It is the same with VPNs, proxies and other anonymity networks.
Tor: The Best Way to Maintain Anonymity Online
Tor is based on the tireless work of thousands of volunteers from around the world. It should be your first port of call if you want to maintain your privacy online. While it is not a silver bullet that will protect you against all forms of cyber-threats, it is certainly a good start. So are you planning to start using Tor to avoid online fingerprinting? Or have you already been using for a while? Let us know in the comments down below. Meanwhile, since you’re interested in online privacy, you should also check out popular encrypted messaging apps, like Signal and Telegram. If you’re using WhatsApp, you can follow our guides to switch over to Signal or Telegram from the Facebook-owned service. You can also learn how to use Signal on desktops and on Chromebooks to chat with your friends, family and colleagues while working.